What Happens When a Database Hits Its Connection Limit
Master database architecture and prevent global outages. Learn how connection limits cause thread starvation, and how to scale using connection pooling, database proxies, and read replicas.
This blog covers:
Exploring database connection limits
Understanding server resource exhaustion
Tracing cascading system failures
Implementing efficient connection pooling
Scaling backend architecture safely
Building reliable software architectures requires a deep understanding of strict hardware limitations. Frontend web servers might operate perfectly during high traffic events. The source code might be fully optimized and bug-free.
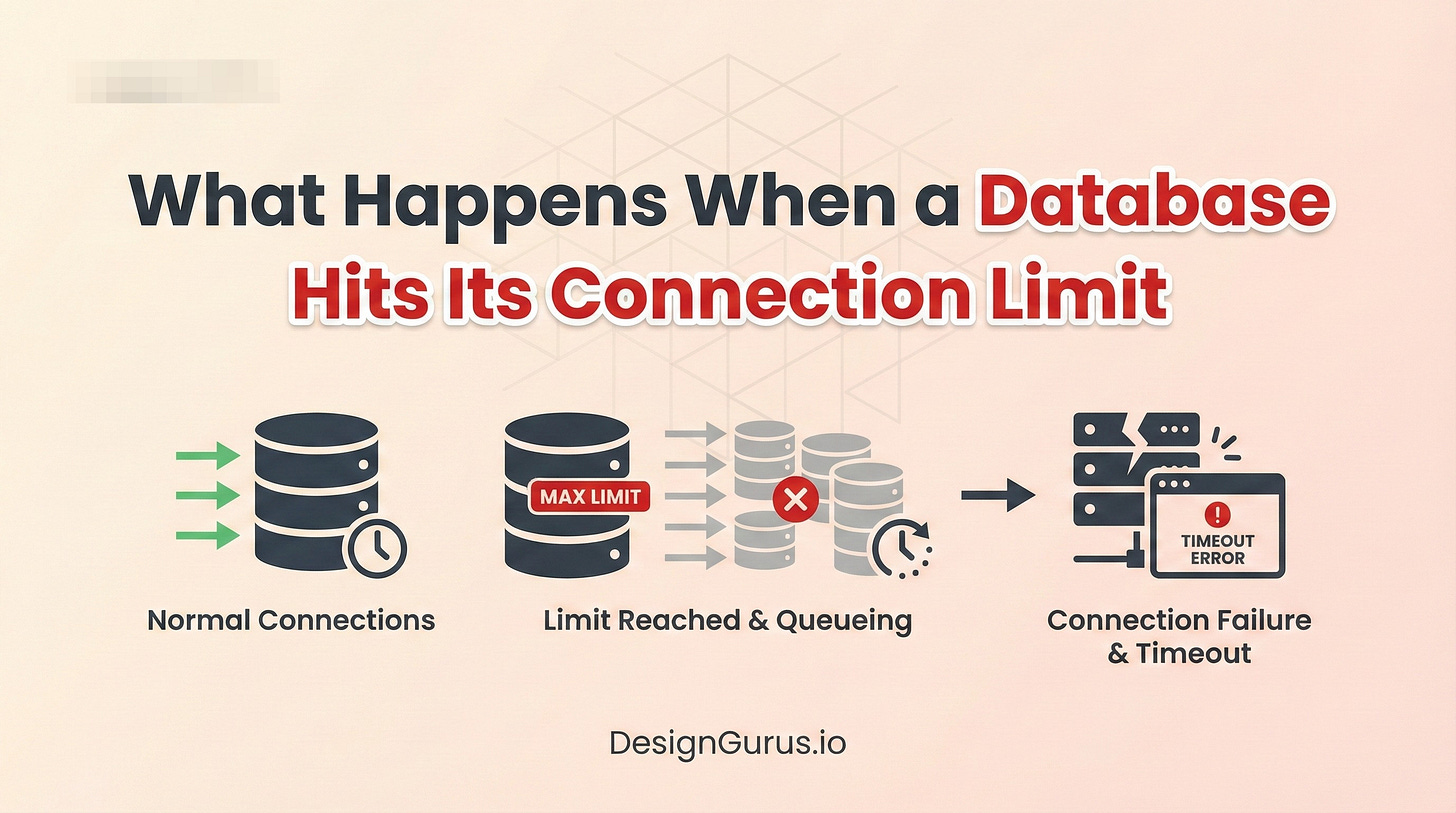
Yet the entire backend infrastructure can suddenly stop responding.
This specific failure often indicates a severe bottleneck in the data storage layer.
The primary database simply reaches its maximum capacity for new network connections. Understanding this exact bottleneck is a fundamental requirement for mastering large-scale system design. It is the core reason why distributed systems fail under intense pressure.
Understanding Database Connections
To understand the failure, one must first understand the database connection itself.
A database connection is a dedicated network communication pathway. It exists strictly between an application server and a database server. Creating this pathway requires significant computational work from both machines.
The servers cannot simply send data back and forth instantly.
The process begins with a complex network handshake.
The application server sends a preliminary network packet to the database server. The database server acknowledges this packet and responds.
The application server then sends a final confirmation back to complete the connection. This multi-step initialization establishes a secure communication channel.
After the network layer connects, the database must verify security credentials. The application server transmits an encrypted password.
The database software checks these details against its internal security records.
Only after successful authentication does the database allow actual data queries. This entire setup process takes valuable processing time.
The Hidden Hardware Costs
Each open connection consumes physical system resources.
A database connection is not just a theoretical software concept. It requires dedicated physical hardware allocation on the database server.
The database software explicitly reserves memory for every single active connection.
This reserved memory is absolutely critical for data processing.
The database uses it to track incoming queries and buffer the outgoing results. Even if a connection sits completely idle, it still holds onto this allocated memory.
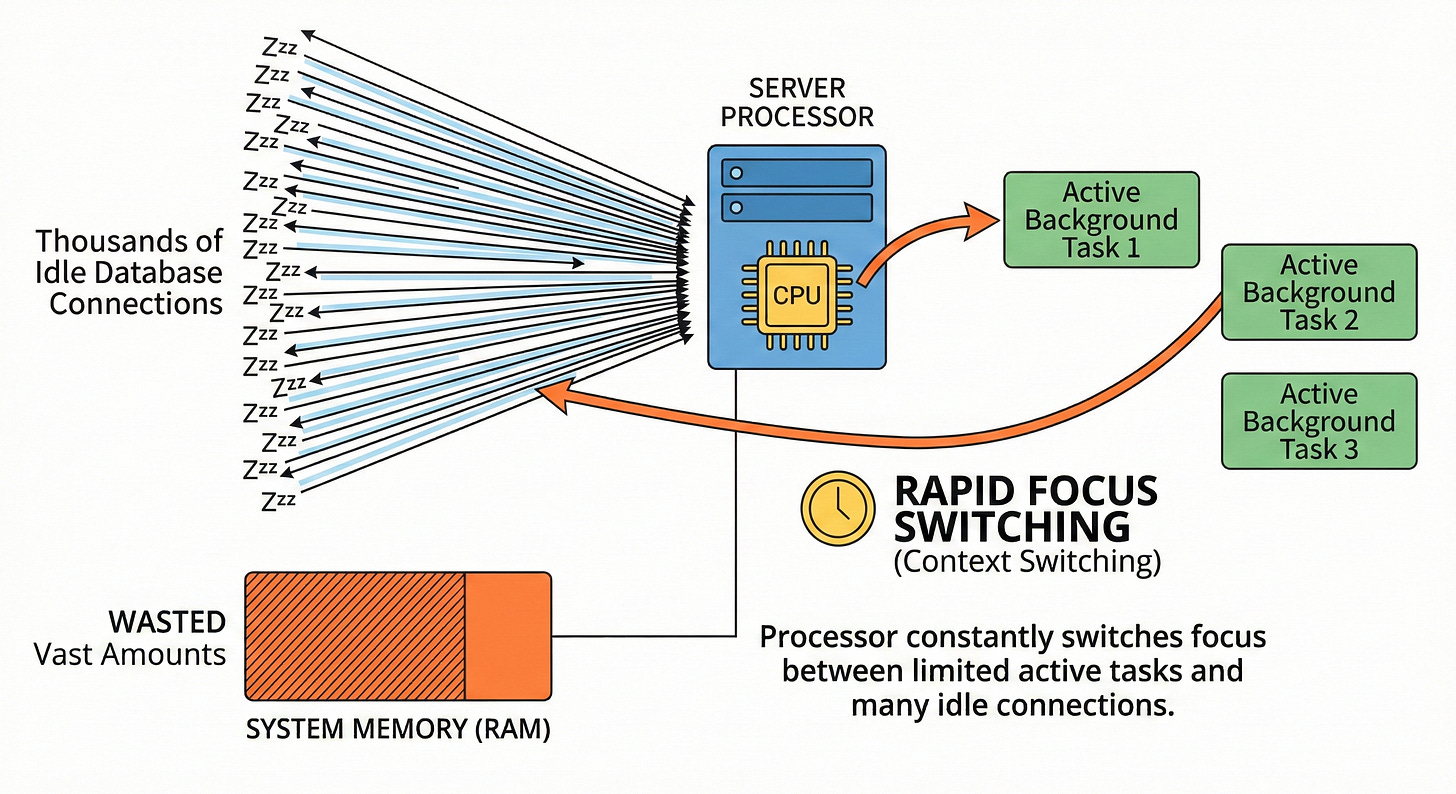
Having thousands of idle connections wastes vast amounts of available system memory.
The server processor also tracks these open pathways constantly.
A computer processor can only handle a specific number of background tasks simultaneously. Managing many open database connections forces the processor to rapidly switch its focus.
This continuous switching is known as context switching.
Excessive context switching severely degrades overall server performance. The processor spends more time managing network connections than actually executing database queries.
Why Databases Enforce Hard Limits
Databases cannot accept an infinite number of connection requests.
Hardware resources have absolute physical boundaries that cannot be bypassed.
A server only has a finite amount of physical memory. It only has a specific number of processor processing cores.
If a database tries to process too many concurrent connections, it will exhaust its memory entirely.